'Iranian Cyber Army' attack leaves Twitter users searching for new activities
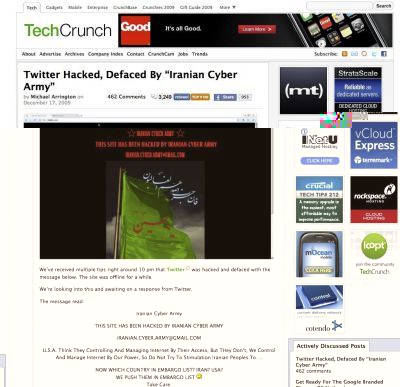
Twitter's DNS (Domain Name System) records were "temporarily compromised" on the evening of December 17 causing the site to be re-directed to a page displaying the message, "This site has been hacked by Iranian Cyber Army."
"Twitter's DNS records were temporarily compromised tonight but have now been fixed," wrote Biz Stone, co-founder of Twitter, in a December 17 post on Twitter's official blog. "As some noticed, Twitter.com was redirected for a while but API and platform applications were working. We will update with more information and details once we've investigated more fully."
According to technology blog TechCrunch, the site redirected Twitter users to a page showing an image of the Iranian flag with a message that read:
"Iranian Cyber Army. THIS SITE HAS BEEN HACKED BY IRANIAN CYBER ARM. iRANiAN.CYBER.ARMY@GMAIL.COM. U.S.A. Think They Controlling And Managing Internet By Their Access, But THey Don't, We Control And Manage Internet By Our Power, So Do Not Try To Stimulation Iranian Peoples To....NOW WHICH COUNTRY IN EMBARGO LIST? IRAN? USA? WE PUSH THEM IN EMBARGO LIST. Take Care."
As soon as the site came back on line a flood of tweets with the hashtag "#whentwitterwasdown" spread across the microblogging site as users wrote about the ways in which they occupied their time while Twitter was down.
On December 15 Twitter declared that "Iranian elections" was the most engaging topic of the year on the microblogging site. The terms "#iranelection", "Iran" and "Tehran" were all in Twitter's list of the top-21 Trending Topics for 2009.
http://www.techcrunch.com/2009/12/17/twitter-reportedly-hacked-by-iranian-cyber-army/
Subscribe to Independent Premium to bookmark this article
Want to bookmark your favourite articles and stories to read or reference later? Start your Independent Premium subscription today.

Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies